MikroTik Tutorial: Firewall ruleset for IPsec whitelisting
This article will show you how to setup a firewall whitelist for IPsec peer associations on a MikorTik router. The firewall ruleset will make use of address-lists to allow UDP 500 traffic only from trusted networks.
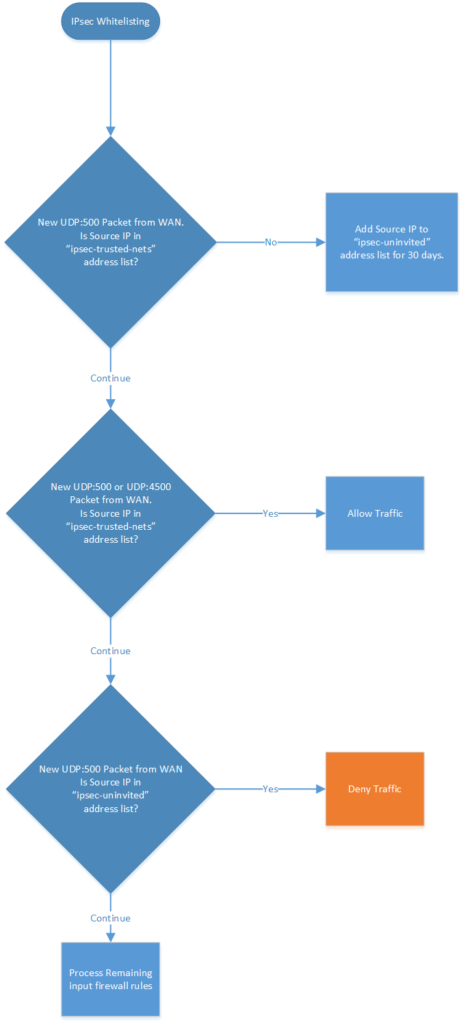
The address list for trusted networks will be called ipsec-trusted-nets and all other hosts that attempt IPsec traffic will be added to the list ipsec-uninvited.
Here are the firewall input rules
Please Note: This is not a complete firewall ruleset, only the rules relevant to whitelist/blacklist IPsec traffic to the router.
/ip firewall filter
add action=add-dst-to-address-list address-list=ipsec-uninvited \
address-list-timeout=4w2d chain=input comment=\
"Add unknown IPsec attempts to \"ipsec-uninvited\" list" connection-state=new \
dst-port=500 in-interface=ether1 protocol=udp src-address-list=\
!ipsec-trusted-nets
add action=accept chain=input comment=\
"Allow UDP:500 from \"ipsec-trusted-nets\" list" dst-port=500 in-interface=\
ether1 protocol=udp src-address-list=ipsec-trusted-nets
add action=accept chain=input comment=\
"Allow UDP:4500 to ADDRESS-LIST:ipsec-trusted-nets" dst-port=4500 in-interface=\
ether1 protocol=udp src-address-list=ipsec-trusted-nets
add action=drop chain=input comment="Deny UDP:500 from \"ipsec-uninvited\" list" \
dst-port=500 in-interface=ether1 log=yes log-prefix=ipsec-uninvited protocol=udp \
src-address-list=ipsec-uninvited
Decision Flowchart
This technique will limit the total attack surface of your public facing IPsec VPN router. I know that all of my IPsec clients will be coming from one class A subnet (owned by one of the major wireless carriers) so I’ve added it to the ipsec-trusted-nets address list. The same technique can be used to whitelist/blacklist other protocols such as SSH.
If you found this articles useful please take a moment to share it on twitter! Join the conversartion by writing a comment below or check my other Mikrotik Tutorials.

LinkRunner G2 is the ultimate network cable test tool
CAT5 Cable Tester, Measure Cable Length,
PoE Voltage, Network Connectivity, Switch Port ID
Optional Wireless & Fiber Optics Modules
Check Price on Amazon