
MikroTik Script: Authentication Logging w/ Email Reports
In this article I will show you how to configure a separate log file on a MikroTik router that will only contain authentication log entries. The log file will contain log entries for winbox, webfig, ssh, telnet, ftp as well as VPN user authentications. Additionally, we will configure a scheduled script to email this log file to ourselves daily.
If you haven’t already, now is a good time to stop and configure logging to disk on your MikroTik router.
Configure Authentication Logging to a dedicated log file
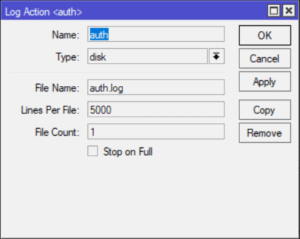
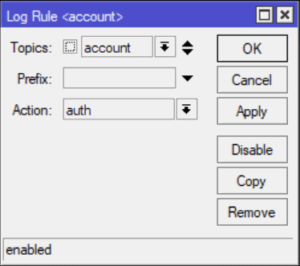
/system logging action add disk-file-count=1 disk-file-name=auth.log disk-lines-per-file=5000 name= auth target=disk /system logging add action=auth topics=account
What we have done here is defined a new logging action named `auth` that logs to a file on disk named `auth.log`. In my example the log file will retain the last 5000 entries. The second line tells the MikroTik router to write any new logs with the topic `account` to the `auth.log` file.
If you are using winbox here is what the configuration screens look like.
Important
The above configuration will only log successful authentication events such as login and logout. If you would also like to log authentication failures you will also need to add another logging definition for `critical`. Since there are other non-authentication critical log events they may end up in your `auth.log` file.
/system logging add action=auth topics=critical
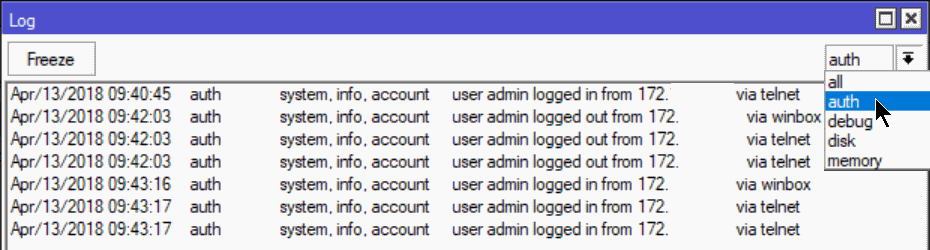
Before we get to the email configuration and script I want to point out that you can now easily filter and view authentication logs from within winbox. Just open the log viewer and choose `auth` from the dropdown.
You can also print the auth log from the cli using the following command.
/log print where buffer="auth"
Email Configuration
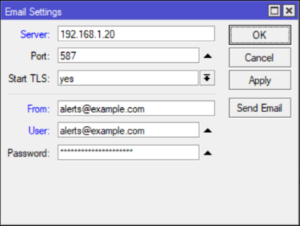
Before we can send email from the MikroTik router we must configure a valid email server in `Tools | Email`. Here is an example, of course you will have to workout your own authentication credentials.
/tool e-mail
set address=192.168.1.20 from=alerts@example.com password=\
super-secret-email-password port=587 start-tls=yes user=alerts@example.com
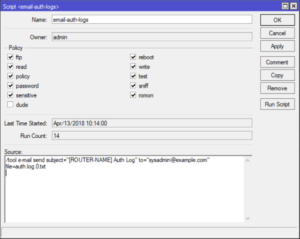
The Script
I have chosen to create a dedicated script and separate schedule that executes the script. I could also just paste the script right into the schedule itself. I like the separated approach because you can run the script on demand from winbox using the `Run Script` button.
/system script
add name=email-auth-logs owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="/to\
ol e-mail send subject=\"[ROUTER-NAME] Auth Log\" to=\"sysadmin@example.com\
\" file=auth.log.0.txt"
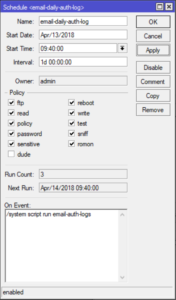
The Schedule
/system scheduler
add interval=1d name=email-daily-auth-log on-event=\
"/system script run email-auth-logs " policy=read,write,sensitive \
start-date=apr/13/2018 start-time=09:40:00
The schedule that I have configured emails the auth.log file as attachment everyday at 9:40AM. Here are the equivalent winbox screenshots.
Example Authentication Log Entries
# login via telnet 09:40:45 system,info,account user admin logged in from 192.168.x.xxx via telnet # login via winbox 09:42:03 system,info,account user admin logged in from 192.168.x.xxx via winbox # login via webfig (http) 11:08:36 system,info,account user admin logged in from 192.168.x.xxx via web # login via L2TP/IPSec VPN 11:10:27 l2tp,ppp,info,account vpnuser logged in, 192.168.xx.xx 11:10:34 l2tp,ppp,info,account vpnuser logged out, 7 1939 7759 21 20 # login via ssh 11:11:38 system,info,account user admin logged in from 192.168.x.xxx via ssh # login via ftp 11:12:45 system,info,account user admin logged in from 192.168.x.xxx via ftp 11:12:53 system,info,account user admin logged out from 192.168.x.xxx via ftp
I hope you find this technique useful in monitoring and managing your MikroTik devices. Feel free to leave a comment below or checkout my other MikroTik Tutorials.

LinkRunner G2 is the ultimate network cable test tool
CAT5 Cable Tester, Measure Cable Length,
PoE Voltage, Network Connectivity, Switch Port ID
Optional Wireless & Fiber Optics Modules
Check Price on Amazon

14 Replies to “MikroTik Script: Authentication Logging w/ Email Reports”
Hello, thanks for the information.
Is it possible to define it only with access by winbox?
Or winbox and www?
If I understand you correctly, you are wanting to filter down the list of log events to only include winbox and web logins (successful logins and login failures).
The following command will query all logs for winbox and webfig authentication events and write them to a new file. Then you can augment the script to email that file instead.
worked peeeerfectly! Thank you!
hi, pls help me, how send to email if mikrotik find new log
how to logging user & password?
because in this tutorial is username only can save to log file
The password is not logged
ow, how to get the password?
myabe can get from packet sniffing?
Hello my friend.
Is it possible to configure alerts when a specific user logged in (for example my_user), and not everyone who is logged in?
Similar to one of the above comment replies you can search the log for a specific user’s login.
You could redirect the results to a file and then modify the script to email targetuser.log instead.
Of course this will not be a real-time alert but sent on a schedule. Real-time login alerts are possible but it’s somewhat involved. You would need to study up on the Log Parser script found in the Mikrotik Wiki https://wiki.mikrotik.com/wiki/Log_Parser_-_Event_Trigger_Script
Or send alerts about the login of all users, with the exception of one (my_user)?
This will print all log entries for the topic system,info,account where the string “my_user” is not present.
Hello, can you please advise about a script that send email and contains log for each wrong wifi password entry with the entered keywords, say once daily
Hi, I would change <> to <>. Than you get the hostname resolved on its own.
Hi, I would change “subject=\”[ROUTER-NAME]” to “subject=\”$[/system identity get name]”. Than you get the hostname resolved on its own.