
MikroTik Config: cAP Lite Wifi Router w/L2TP VPN & Guest Wifi
This is an example configuration file for the MikroTik cAP Lite. The cAP Lite is a tiny access point device w/ full RouterOS router functionality. The router features 1 10/100 ethernet interface and can be powered with 5V MicroUSB or any PoE inject 10-60V.
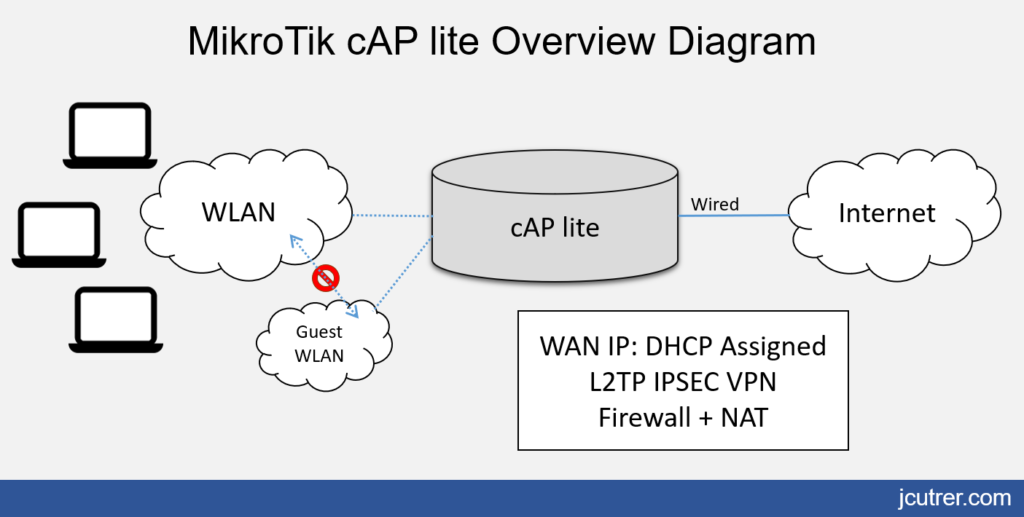
Config Features
- Wired WAN
- Wifi LAN
- Firewall/NAT
- Isolated Guest Wifi Network
- L2TP over IPSec Remote Access VPN
Configuration File Home AP+Router w/L2TP VPN & Guest Wifi
# nov/30/2017 14:01:27 by RouterOS 6.40.5
# reference = https://jcutrer.com/howto/networking/mikrotik/mikrotik-rbcapl-…e-config-home-ap
# revision = 1.0
# model = RouterBOARD cAP L-2nD
/interface bridge
add comment="LAN Bridge" name=bridge
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n channel-width=20/40mhz-Ce comment=Wifi \
country="united states" disabled=no distance=indoors frequency=auto mode=ap-bridge \
rx-chains=0,1 ssid="MikroTik" tx-chains=0,1 wireless-protocol=802.11
/interface wireless manual-tx-power-table
set wlan1 comment=Wifi
/interface wireless nstreme
set wlan1 comment=Wifi
/ip neighbor discovery
set ether1 discover=no
# Wifi Security Settings
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa-psk,wpa2-psk eap-methods="" mode=\
dynamic-keys supplicant-identity=MikroTik wpa-pre-shared-key=mywifisecret \
wpa2-pre-shared-key=mywifisecret
# Guest Wifi Security Settings
add authentication-types=wpa-psk,wpa2-psk eap-methods="" mode=dynamic-keys name=profile-guest \
supplicant-identity=MikroTik wpa-pre-shared-key=guestpassword wpa2-pre-shared-key=\
guestpassword
# Guest Wifi Interface
/interface wireless
add comment="Guest Wifi" disabled=no master-interface=wlan1 \
name=wlan2 security-profile=profile-guest ssid="MikroTik-Guest"
/interface wireless manual-tx-power-table
set wlan2 comment="Guest Wifi"
/interface wireless nstreme
set wlan2 comment="Guest Wifi"
/ip hotspot profile
set [ find default=yes ] html-directory=flash/hotspot
/ip pool
add name=dhcp ranges=192.168.1.100-192.168.1.254
add name=vpn ranges=192.168.89.100-192.168.89.254
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=dhcp1
/ppp profile
set *FFFFFFFE local-address=192.168.89.1 remote-address=vpn
/interface bridge filter
add action=drop chain=forward comment="Isolate Guest Wifi" in-interface=wlan2
add action=drop chain=forward comment="Isolate Guest Wifi" out-interface=wlan2
/interface bridge port
add bridge=bridge comment=defconf disabled=yes interface=ether1
add bridge=bridge comment=defconf interface=wlan1
add bridge=bridge interface=wlan2
/ip firewall connection tracking
set tcp-established-timeout=5h
# Enable L2TP Server and Set PreShared Key
/interface l2tp-server server
set enabled=yes ipsec-secret=myvpnsecret use-ipsec=yes
/ip address
add address=192.168.1.1/24 interface=wlan1 network=192.168.1.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-client
add comment=defconf dhcp-options=hostname,clientid disabled=no interface=ether1
/ip dhcp-server network
add address=192.168.1.0/24 gateway=192.168.1.1 netmask=24
# Begin Firewall Rules
/ip firewall filter
add action=accept chain=input comment="Allow Ping (icmp)" protocol=icmp
add action=accept chain=input comment="Allow established" connection-state=established
add action=accept chain=input comment="Allow related" connection-state=related
add action=accept chain=input comment="allow L2TP VPN (ipsec-esp)" protocol=ipsec-esp
add action=accept chain=input comment="allow L2TP VPN (1701/udp)" dst-port=1701 protocol=udp
add action=accept chain=input comment="allow L2TP VPN (4500/udp)" dst-port=4500 protocol=udp
add action=accept chain=input comment="allow L2TP VPN (500/udp)" dst-port=500 protocol=udp
add action=drop chain=input comment="Deny All input from WAN" in-interface=ether1
add action=drop chain=forward comment="deny new,invalid,untracked connections" \
connection-state=invalid,new,untracked in-interface=ether1
add action=accept chain=forward comment="allow established,related connections" \
connection-state=established,related in-interface=ether1
add action=drop chain=forward comment="deny All forward from WAN" in-interface=ether1
# Begin NAT Rules
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1
add action=masquerade chain=srcnat comment="masq. vpn traffic" src-address=192.168.89.0/24
# Disable Unneeded IP Services
/ip service
set telnet disabled=yes
set ftp disabled=yes
set api disabled=yes
set api-ssl disabled=yes
# VPN User Account
/ppp secret
add name=vpnuser password=vpnpass
/system clock
set time-zone-name=America/New_York
/tool mac-server
set [ find default=yes ] disabled=yes
add interface=wlan1
add interface=wlan2
/tool mac-server mac-winbox
set [ find default=yes ] disabled=yes
add interface=wlan1
add interface=wlan2
Download this File cap-lite-example-config.rsc
Customize Before Use
Before you use the above configuration in your router you will want to change the WiFi SSIDs, Wireless Password, L2TP Shared Secret, PPP username/password.
- Line 10: Wireless SSID
- Line 29: Guest Wireless SSID
- Line 20-21: Wireless Password
- Line 24-25: Guest Wireless Password
- Line 54: IPSec Secret (PreShared Key)
- Line 85: VPN username & password
Configuration Details
- WAN Interface: ether1 (IP:DHCP Assigned)
- LAN Interface: bridge (IP: 192.168.1.1)
- Wifi Interface: wlan1 (SSID: Mikrotik)
- Guest Wifi Interface: wlan2 (SSID: Mikrotik-Guest)
- LAN Subnet: 192.168.1.0/24
- DHCP Pool: 192.168.1.100-192.168.1.254
- VPN Pool: 192.168.89.100-192.168.89.254
References
cAP Lite Model Number: RBcAPL-2nD
What’s Next? Checkout my other MikroTik Tutorials!

LinkRunner G2 is the ultimate network cable test tool
CAT5 Cable Tester, Measure Cable Length,
PoE Voltage, Network Connectivity, Switch Port ID
Optional Wireless & Fiber Optics Modules
Check Price on Amazon

3 Replies to “MikroTik Config: cAP Lite Wifi Router w/L2TP VPN & Guest Wifi”
Very nice tutorial. Thanks for your time.
I’m trying to use this tutorial as a starting point for my need. I’m using a different configuration, which requires that the wifi port in your tutorial also has some hard wired ports. I’m using a RB 2011 as the main router with a RB951 for the wireless radio. Some of the ports on the 2011 are on the main subnet while other ports are on the guest subnet. I don’t see how to do this. Can you please point me in the correct direction.
Peace,
Pat
I would suggest creating a separate bridge interface and dhcp scope for the guest network. Then the second (guest) IP subnet will be assigned to that bridge. The guest wifi interface and an wired (guest) ports will also be assigned to that bridge.
Finally, you will need to modify your bridge filter rules to maintain proper isolation between the two networks. Good luck!
Thanks for this amazing guide i really loved it. i was looking for this networking config for my