MikroTik: L2TP/IPsec VPN Firewall Rules
When you configure a L2TP/IPSec VPN on a MikroTik RouterOS device you need to add several IP Firewall (Filter) rules to allow clients to connect from outside the network.
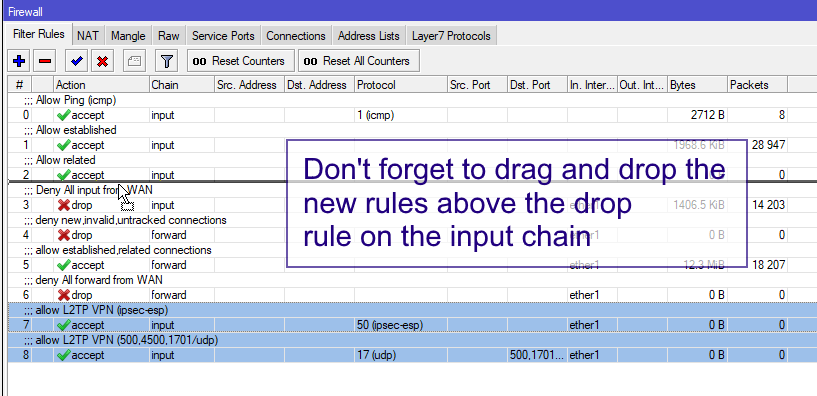
L2TP/IPSec Firewall Rule Set
/ip firewall filter
add action=accept chain=input in-interface=ether1 protocol=ipsec-esp \
comment="allow L2TP VPN (ipsec-esp)"
add action=accept chain=input dst-port=1701 in-interface=ether1 protocol=udp \
comment="allow L2TP VPN (1701/udp)"
add action=accept chain=input dst-port=4500 in-interface=ether1 protocol=udp \
comment="allow L2TP VPN (4500/udp)"
add action=accept chain=input dst-port=500 in-interface=ether1 protocol=udp \
comment="allow L2TP VPN (500/udp)"These rules must be placed above any deny rules on the “input” chain.
The ruleset can be further condensed by combining the 3 udp rules into one.
/ip firewall filter
add action=accept chain=input in-interface=ether1 protocol=ipsec-esp \
comment="allow L2TP VPN (ipsec-esp)"
add action=accept chain=input dst-port=500,1701,4500 in-interface=ether1 protocol=udp \
comment="allow L2TP VPN (500,4500,1701/udp)"
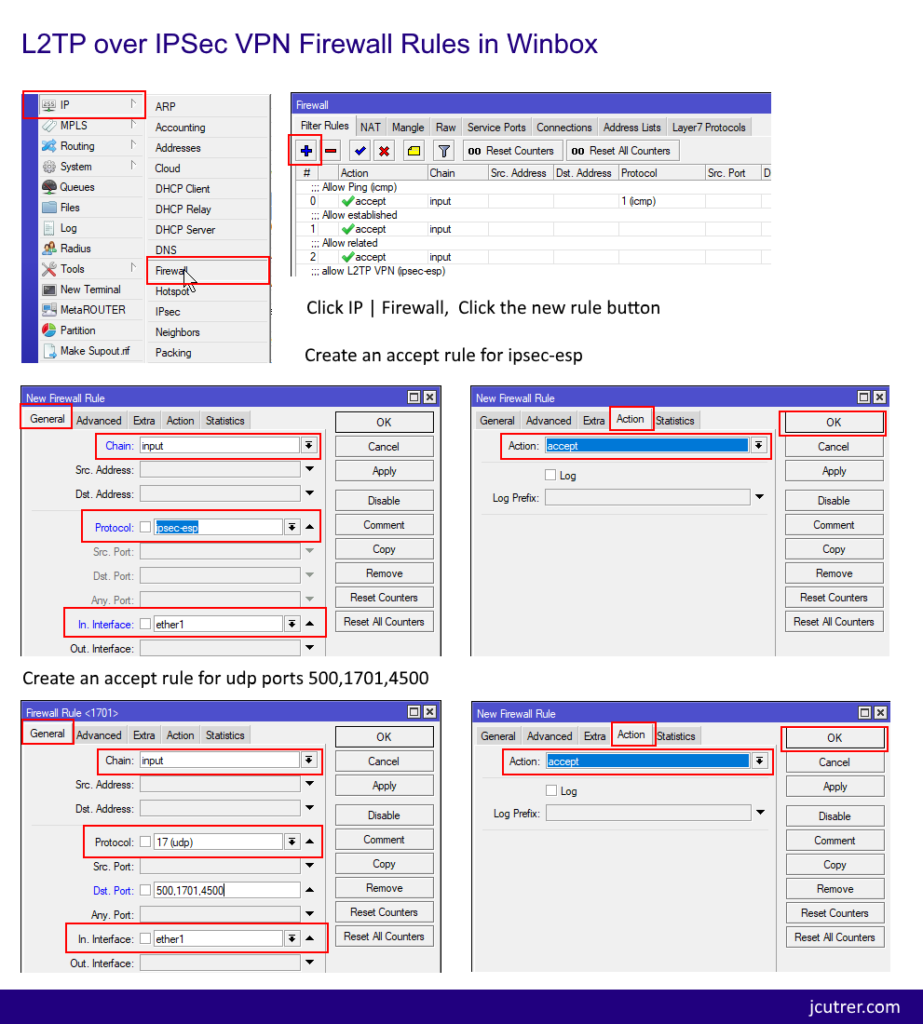
Add these firewall rules in Winbox
If you want to avoid pasting commands into the cli you can create these firewall rules in winbox, here are some screenshots.
Important: Don’t forget to reorder your input rules!
I hope you found this MikroTik Tutorial about L2TP/IPsec VPN Firewall Rules useful. If it helped you out, please leave a comment below and checkout my other MikroTik Tutorials!

LinkRunner G2 is the ultimate network cable test tool
CAT5 Cable Tester, Measure Cable Length,
PoE Voltage, Network Connectivity, Switch Port ID
Optional Wireless & Fiber Optics Modules
Check Price on Amazon

10 Replies to “MikroTik: L2TP/IPsec VPN Firewall Rules”
Hi thanks for the tutorial. Is there a way to test why traffic is being dropped even though connection through Port seems to have been established.
This may help you https://jcutrer.com/howto/networking/mikrotik/l2tp-over-ipsec-troubleshooting
Thanks for the guide. I can connect through vpn, but I am not able to ping local addresses. Is there something else in the firewall?
It may be a NAT issue depending on how the rule is configured. Having a src-nat rule that only has one match defined (outbound WAN interface) should allow the traffic between the VPN Pool IPs and the LAN subnet. I hope that helps.
Very good my Friend! Tnks !!!
saved my day
Hi,
it’s an old post, so, please accept my humble apologies for bothering you.
I am using a pppoe connection to connect to my ISP from my router and I would like to set up a L2TP-IPsec server too on the same router. The client is an old laptop. I watched many tutorials (especially on Youtube), but no one helped me. I feel that something is uncomplete. Maybe I should declare in GUI (the CLI’s commands are awful) in IP -> Firewall -> Filter notes -> add new… IN interface pppoe-out/dynamic (instead WAN/ether1) ?
Off-topic:
I remember my old Cisco router’s config – I used it to forward OpenVPN incoming connections (on a non-standard 7620 port) to other (non-Cisco) router behind…
Without these rules, I couldn’t connect…
!
interface Dialer0
…
ppp ipcp dns request accept
ppp ipcp route default
ppp ipcp address accept
!
…
ip route 0.0.0.0 0.0.0.0 10.0.0.1 # ISP’s gateway’s IP
!
…
ip nat inside source static udp 10.10.10.10 1194 interface Dialer0 7620
…
access-list 103 permit udp any any eq 7620
Thank you very much.
You sir, are a life saver. Works as charm. Thank you!
Hello, I’m having a problem!… I have an RB201, I’m able to connect to a VPN, but the speed is at low company, it didn’t start to grow at 1 MB, I changed an MTU to 1300 and now it reaches 3 MB and note that my CPU when I copy the file goes to 90%, and it doesn’t go beyond 3 MB, what am I doing wrong? or is this RB that does not support?… From now on
I have problem huge traffic from wan. Thanks for tutorial.
But can you explain the 0 to 6 rules mean (allow establihed etc.)?