
Mikrotik L2TP over IPSec troubleshooting
Troubleshooting a MikroTik VPN configuration can be frustrating if you do not know where to look. This article is specifically about troubleshooting L2TP over IPSec Remote Access VPNs on RouterOS.
Below are RouterOS configuration areas that relate to L2TP over IPSec.
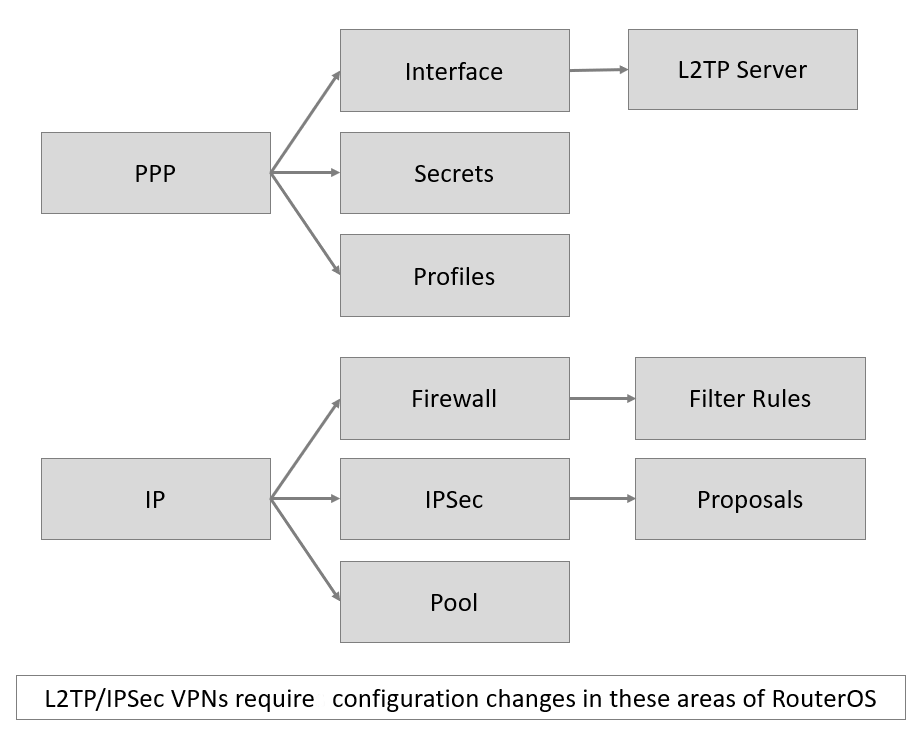
Here are the steps to verify and troubleshoot Remote VPN connections to a MikroTik Router using L2TP over IPSec.
- Ensure that proper firewall ports are open – More info on Mikrotik L2TP/IPSec Firewall Rules here
- Verify that the L2TP server is enabled
- IPSec secret matches on router and client
- Verify that a compatible IPSec proposal is configured
- Verify that PPP Profile and IP Pool is configured
- Make sure PPP username/password matches
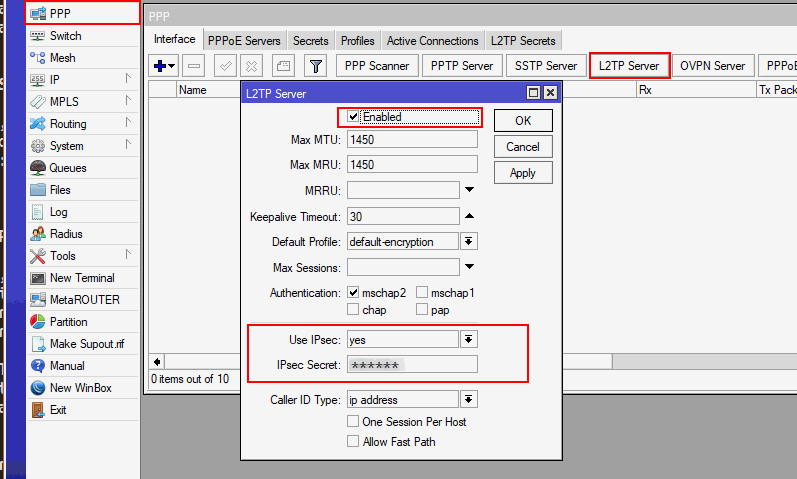
Is your L2TP Server Enabled? Verify IPSec secret (PreShared Key)
- In Winbox, click PPP > Interfaces > L2TP Server
- [x] Enable should be checked
- Use IPSec: yes
- Set IPSec Secret: your-ipsec-psk
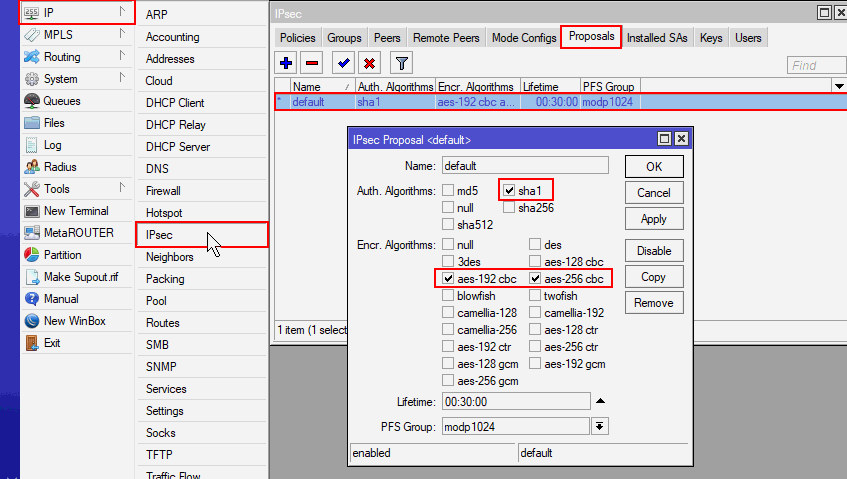
Verify IPSec proposal
- In Winbox, click IP > IPsec > Proposals
- Double click default
- Auth Algorithms: [x] sha1
- Encr. Algorithms: [x] aes-192-cbc, [x] aes-256-cbc
Note: The above proposal is compatible with iOS iPhones / iPads.
If you must support clients older operating systems (such as Windows XP), a different proposal may be required.
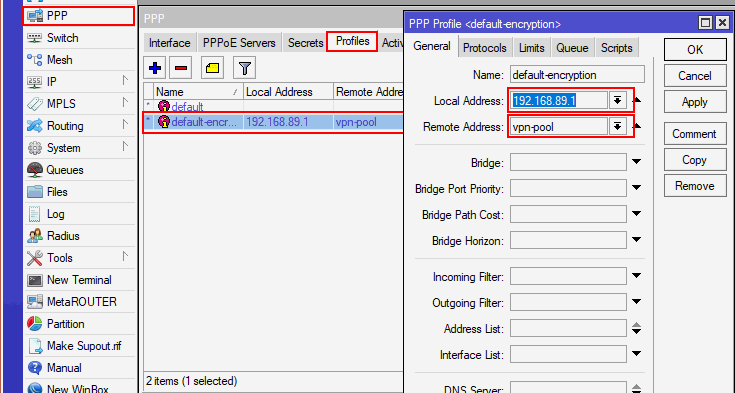
Verify PPP Profile & IP Pool
- In Winbox, click
PPP > Profiles - Default a Local Address
- Specify VPN IP Pool
- If a IP pool needs to be create, goto .IP > Pool
Verify PPP credentials
VPN username accounts are defined in RouterOS as PPP Secrets.PPP > Secrets
Enable IPSec logging
/system logging add prefix="L2TPDBG===>" topics=l2tp
Enable L2TP logging
/system logging add prefix="IPSECDBG===>" topics=ipsec
IPSec Secret (PSK) Mismatch
If you have IPSec logging enable and a client is connecting with an incorrect preshared key you will see the following error in your router’s log file.
14:16:37 ipsec,error IPSECDBG===>: 10.X.X.XX parsing packet failed, possible cause: wrong password
PPP Username/password is incorrect
If you have L2TP logging enable and a client is connecting with an incorrect username or password you will see the following errors in your router’s log file.
14:22:19 l2tp,ppp,debug,packet L2TPDBG===>: 14:22:19 l2tp,ppp,debug,packet L2TPDBG===>: <1X6.XXX.XXX.77>: sent CHAP Failure id=0x1 14:22:19 l2tp,ppp,debug,packet L2TPDBG===>: E=691 R=0 C=A9A0C9CFDEB630268F0DEEEEF55EF149 V=3 M=bad username or password 14:22:19 l2tp,ppp,error L2TPDBG===>: <1X6.XXX.XXX.77>: user vpnuser1 authentication failed
I hope this short guide has helped you troubleshoot & debug Mikrotik L2TP/IPSec VPN configurations. If you have questions, leave a comment below & checkout my other MikroTik Tutorials.

LinkRunner G2 is the ultimate network cable test tool
CAT5 Cable Tester, Measure Cable Length,
PoE Voltage, Network Connectivity, Switch Port ID
Optional Wireless & Fiber Optics Modules
Check Price on Amazon

8 Replies to “Mikrotik L2TP over IPSec troubleshooting”
Excellent, Thank you , work right out of the box, I always avoided L2TP because of the certificate mess on the client side, never found an easy to understand guide, but using it this way without certificates is easy and it works!, thank you!, my mac customers would be very happy hehe.
You will have a tutorial on how to create the certificates or the complete connection for the Mac!
Great tutorial, thank you so much.
I have done quick setup vpn enabled. Is it secure enough or shall disable quickset and start manual ?
Thanks
With your configuration in mikrotik os version 6.40.9 with win10, show an error: no suitable proposal found, why?
I would suggest to add remark cocncerning minimum Ipsec secret length
Thank You! Very clear guide
There is a mismatch in the logging section of this tutorial
Enable IPSec logging (should be L2TP)
/system logging add prefix=”L2TPDBG===>” topics=l2tp
Enable L2TP logging (Should be IPSEC)
/system logging add prefix=”IPSECDBG===>” topics=ipsec
IPSec Proposals for me, thanks!