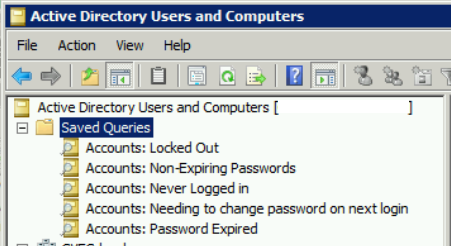
5 Saved Queries to simplify Active Directory administration
In this article I will show you how to build 5 Saved Queries in Active Directory Users and Computers that will make user management a little less painful.

Using Saved Queries, you will be able to quickly see which users are locked out, who’s password has expired and who needs to change their passwords at next login. This article is for IT System Administrators tasked with managing Active Directory Domains.
Before we get started, I want to point out an important bit of information about using Saved Queries. Each time you navigate to a Saved Query, you will need to refresh to trigger the query to rerun. You can accomplish this by pressing the F5 key or by right-clicking on the saved query and choosing “Refresh“.
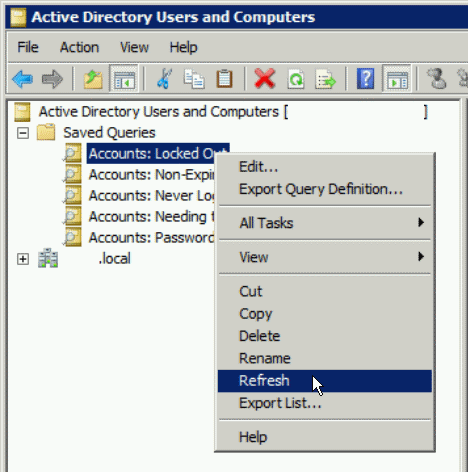
1) Accounts: Locked Out Users
List currently locked out users. This query is helpful when troubleshooting user login issues. Rather than digging through Event Logs or finding the users account in AD, the user will just show up in this list.
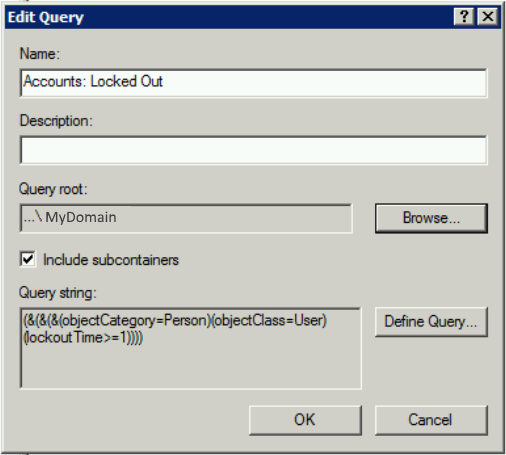
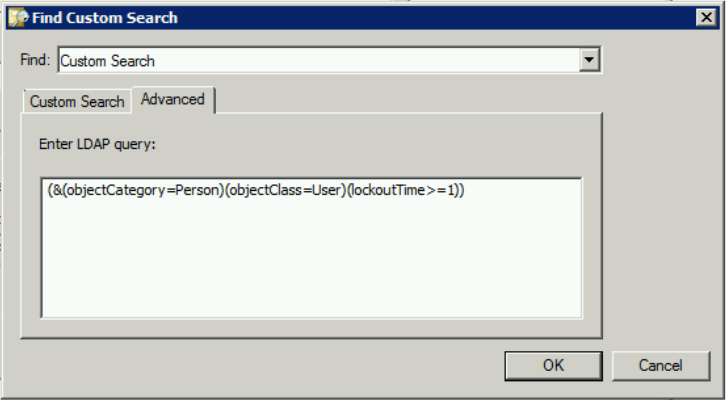
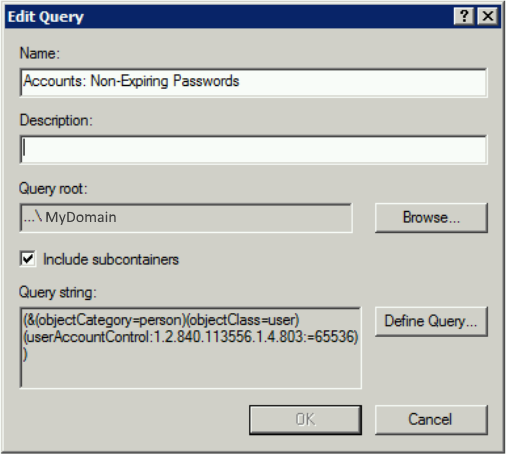
2) Accounts: Non-Expiring Passwords
List users that have “Password never expires” option ticked
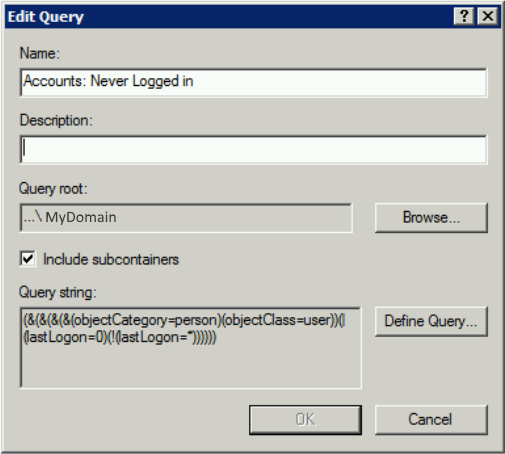
3) Accounts: Never Logged in
List user accounts that have never logged in
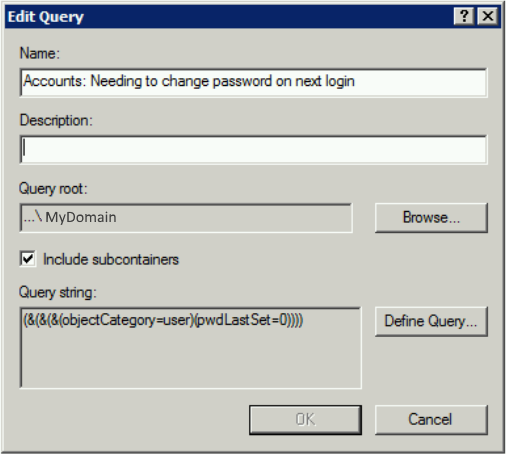
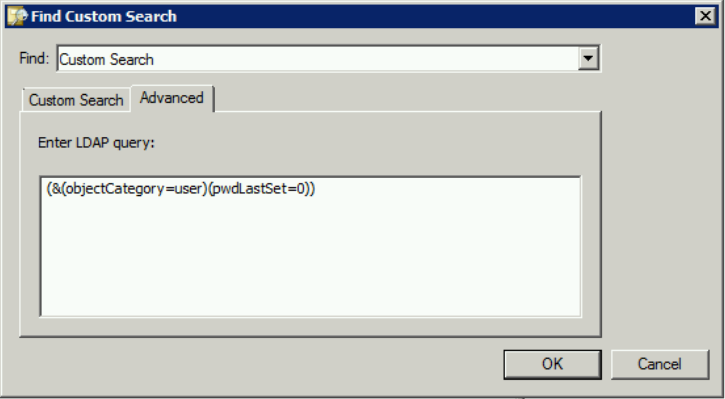
4: Accounts: Needing to change password on next login
This query will list user accounts who are required to change their password at next login
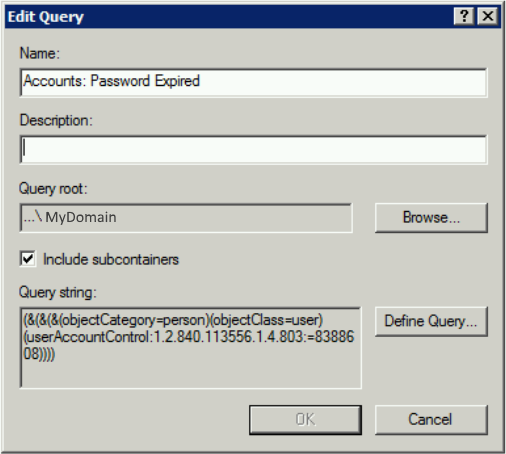
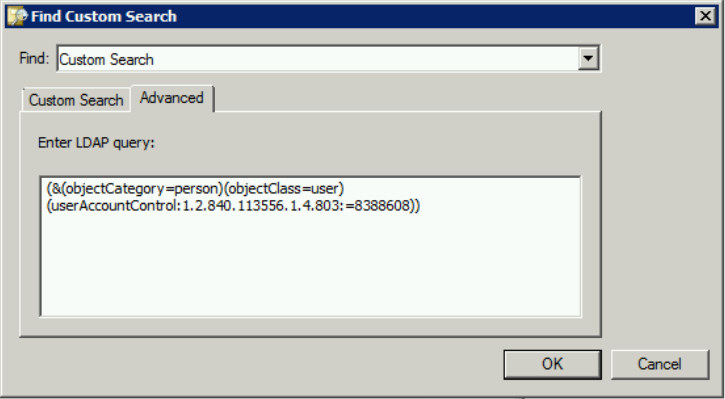
5: Accounts: Password Expired
This query will list user accounts who’s password has expired.
These queries were created and used on a Windows Server 2008 R2 machine. I have not tested them on Server 2012 or Server 2016 but they should work just fine.
Download all 5 Saved Queries from this article here:
jcutrer.com-saved-query-definitions.zip
How to Import Saved Query Definitions
- Download and extract the zip file linked above
- Open “Active Directory Users and Groups”
- Right-click on “Saved Queries” and choose “Import Query Definition”
- Browse to and choose the first xml file
- Repeat above steps for each Query Definition

11 Replies to “5 Saved Queries to simplify Active Directory administration”
Do you use Saved Queries for AD, which ones do you find useful?
Thanks for the info, man.
you should share the code directly instead of throwing the screen image.
You’re welcome, The link to download the query definitions is right in the article.
Thank you for the queries!
Great!
accounts: password expired query doesn’t work on server 2012 r2
When you say it doesn’t work, can you elaborate?
This is a little old, but it doesn’t work in 2012 R2+ domains with fine-grained password policies enabled – the query simply returns zero results.
The way I’ve found to approximate it is to query for enabled accounts with a pwdlastset value greater-than 0 and UAC isn’t set to “password never expires”, then return the msDS-UserPasswordExpiryTimeComputed property from the accounts. The basic query as follows, with a bitwise OR to filter disabled and non-expiring password accounts:
‘(&(samaccounttype=805306368)(pwdLastSet>=1)(!(useraccountcontrol:1.2.840.113556.1.4.804:=65538)))’
Then check each account for msDS-UserPasswordExpiryTimeComputed in the past.
If you know you don’t have fine-grained password policies, you can query pwdLastSet for a value less than your password age, done. Or, if you do have FGPPs and know the maximum interval across all of them, you can use that as the “less-than” value to filter with pwdLastSet, then check msDS-UserPasswordExpiryTimeComputed for individual expiry times.
It’s a right-royal pain in the butt , if it’s something you need to do.
This is a Treasure Trove… I know you have a download for xml versions… Why not just add the code to the site for those that would just like to copy paste and/or modify? Thanks again
Thanks for the suggestion, I will
dear sir thx for your suit doc .
i like to find users that absent in past 90 days and disable them
can i have query related these problem?
Regards Reza